Secure Access Service Edge (SASE), pronounced ‘Sassy’, is a cybersecurity concept originally described by Gartner in its August 2019 report ‘The Future of Network Security in the Cloud’.
Gartner’s 2021 Strategic Roadmap for SASE Convergence report recommends security and risk management leaders develop a roadmap for adoption of SASE.
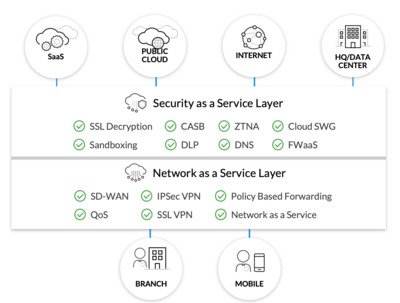
But what is SASE? At its heart, the SASE model is the combination of branch networking technologies such as SD-WAN and VPN with cloud-delivered security services such as Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA) and Firewall-as-a-Service (FWaaS). Such a model allows for provision of branch sites and remote users with minimal infrastructure, whilst ensuring full security capabilities can be offered.
Source: Palo Alto Networks
Traditional network security architectures were designed around providing access to central enterprise data centres. These models have augmented over time to compensate for cloud computing and work from home initiatives — the latter having been greatly accelerated due to COVID-19. With many users and applications now outside of the enterprise, these access requirements are changing.
The multitude of vendors and security solutions deployed across the perimeter today should be addressed by considering how a cloud-delivered model of security may ensure consistent policy and protection.
The SASE security model is likely to help organisations in a number of ways:
- Reduce complexity — Consolidating existing security stacks into a cloud-based service model will minimise the number of security products being operated, supported and maintained.
- Increase performance — Minimising branch site infrastructure in preference to cloud-based models allows scaling when and where it is needed.
- Cost savings — Investing in a single vendor platform reduces the number of point products being procured and managed.
- Flexibility — Security services can be delivered from the cloud as required for each asset being protected.
- Zero trust — A SASE solution will provide complete session protection, regardless of whether users are on or off the enterprise network.
While a full SASE implementation may not be on the cards for all organisations today, there are a number of initiatives that can be considered in starting a journey towards the SASE security model. Organisations should:
- Consolidate vendors as perimeter security products are refreshed and renewed, with the view to have a single SASE vendor.
- Consider cloud-based security services covered by the SASE model as existing hardware products are refreshed.
- Consider minimal-infrastructure deployments to WAN sites, offloading security to the cloud.
- Consider replacing existing remote user VPN connections with a Zero Trust model.
- Engage network and security teams closely to ensure a common solution set can be deployed with shared responsibility.
Many organisations are now transitioning through their SD-WAN journey in order to reduce legacy WAN provider costs and uplift remote site bandwidths through local Internet breakout. As a result, these organisations are having to consider how to apply an equivalent, or better, security posture across the environment. SASE could well be the answer.